![]()
In this blog, I’ll provide some quick tips, Q&As, and useful links from Day 1 of our just introduced new batch of Cloud Security for Azure, AWS, Google Cloud, and Oracle, in which we’ve covered 18+ hands-on labs.
We discussed general cloud security concepts, such as why cloud security is important? Different aspects of cloud security and various cloud security models in our Day 1 Live Session. And finally, we saw the market’s top cloud service providers.
So, here are some of the Q&As asked during the Live session of Day 1 of Cloud Security For Azure, AWS, Google Cloud & Oracle.
What is Cloud Computing and How Does It Work?
Cloud computing delivers computing services over the internet (the cloud), such as servers, storage, databases, networking, software, analytics, and intelligence, to enable faster innovation, more flexible resources, and cost savings. You typically only pay for the cloud services you use, which allows you to save money, run your infrastructure more efficiently, and scale as your company grows.
Learn more about Cloud Fundamental
Cloud computing provides a variety of services based on three main deployment models. They are in the following order: SaaS (Software as a Service), PaaS (Platform as a Service), and IaaS (Infrastructure as a Service) (Infrastructure as a service).
Check more on Cloud Services Models.

Cloud Security Engineer
Cloud Security Engineers identify dangers to cloud systems, design new features to meet security needs, and construct, maintain, upgrade, and improve cloud-based systems.
They can obtain titles such as Cloud Security Architect, Data and Cloud Security Analyst, Security Operations Expert – Cloud, and Cloud Security Engineer, to name a few.

What is the Importance of Cloud Security?
As more data and apps transfer to the cloud, IT employees are concerned about security, governance, and compliance challenges. They are concerned that unintentional leaks or increasingly sophisticated cyber-attacks may compromise extremely sensitive corporate data and intellectual property.
Security threats are continually evolving and growing more sophisticated. As a result, it’s critical to work with a cloud provider that provides best-in-class security that’s tailored to your architecture.
Learn more about Best Practices for Azure Security in 2021
Q1. What are the risks associated with cloud security?
Ans. The global public cloud services market, according to Gartner, will grow 17% to $266.4 billion in 2020, up from $227.8 billion in 2019. And with this rise in the market comes the risk.
The following are a few of the most common cloud computing threats:
- Breach of personal information
- Getting access to a user’s account
- Internal Threat
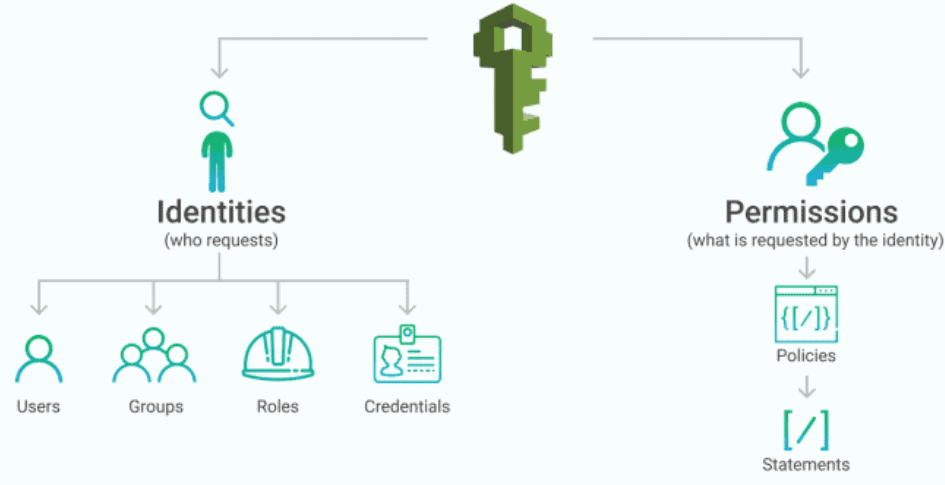
- Inadequate identity, credential, access, key management and many as shown in the picture below
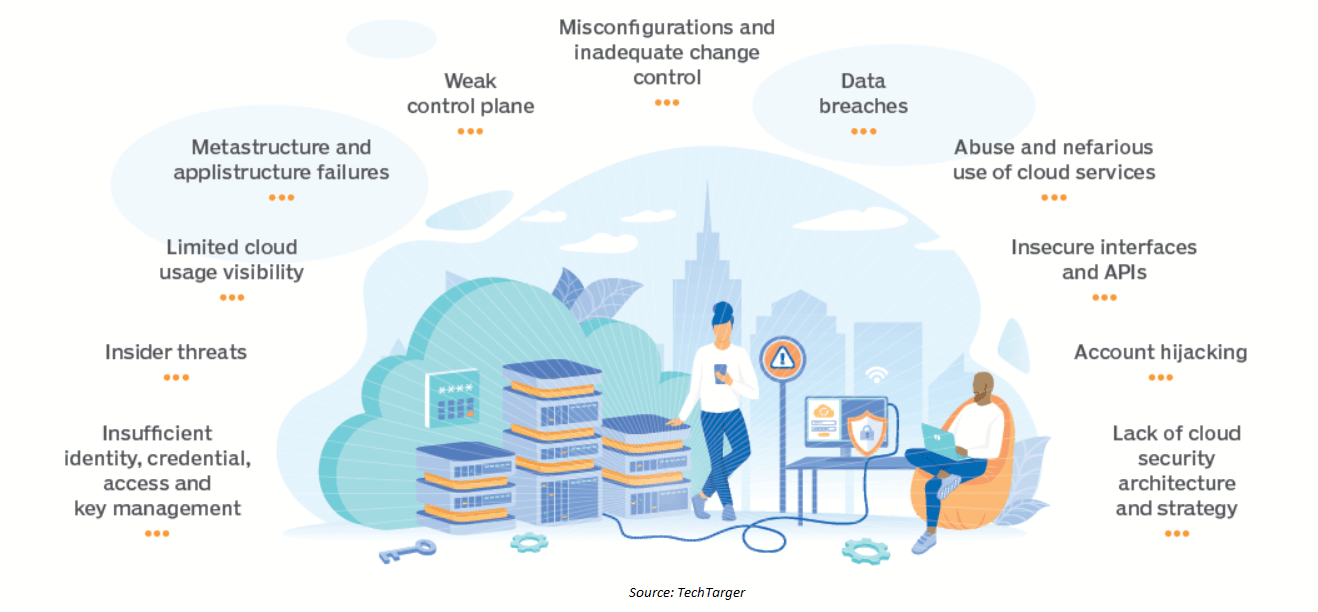
Despite the fact that security is a major barrier to mainstream cloud computing adoption, a collection of cloud enterprises is doing everything they can to provide information security services by securing our network, application, access and identity, container, and database.
Q2. Do cloud security providers adhere to any standards or templates?
Ans. Based on the level of security that the business is working with, standards and templates differ from one organization to the next. Every business deals with a variety of clients, each with its own set of requirements. As a result, the optimal approach will be determined by the organization’s needs.
Now lets us dive into the security aspects of cloud one by one, starting with network security:
Network Security
An organization’s network capabilities and resources are housed in a private or public cloud platform, maintained in-house or by a service provider, and made available on demand. As a result, a network serves as the backbone of an organization. All data enters and exits through the network. Because, unlike on-premise, where only company employees may access the resources, the cloud is housed on the internet, where anybody can access the resources; consequently, network security is critical.

Today’s public cloud security uses four increasing protection levels:
- Security Groups: Which provides the first layer of cloud network security protection and are responsible for traffic rules.
- Network Access Control Lists (NACLs): Each NACL is linked to a Virtual Private Network (VPC) or a Virtual Network (VNet). NACLs control all instances in that VPC or VNet.
- Cloud Vendor Security Solution: The vendors, from time to time, includes their own solutions to get an edge in the market. For example, FWaaS- a next-generation secure internet gateway that functions as a barrier between the cloud and the internet.
- 3rd Party Cloud Security Solution: These third parties build firewalls between public clouds and the rest of the world and segment the cloud’s inner perimeter like an on-premise network.
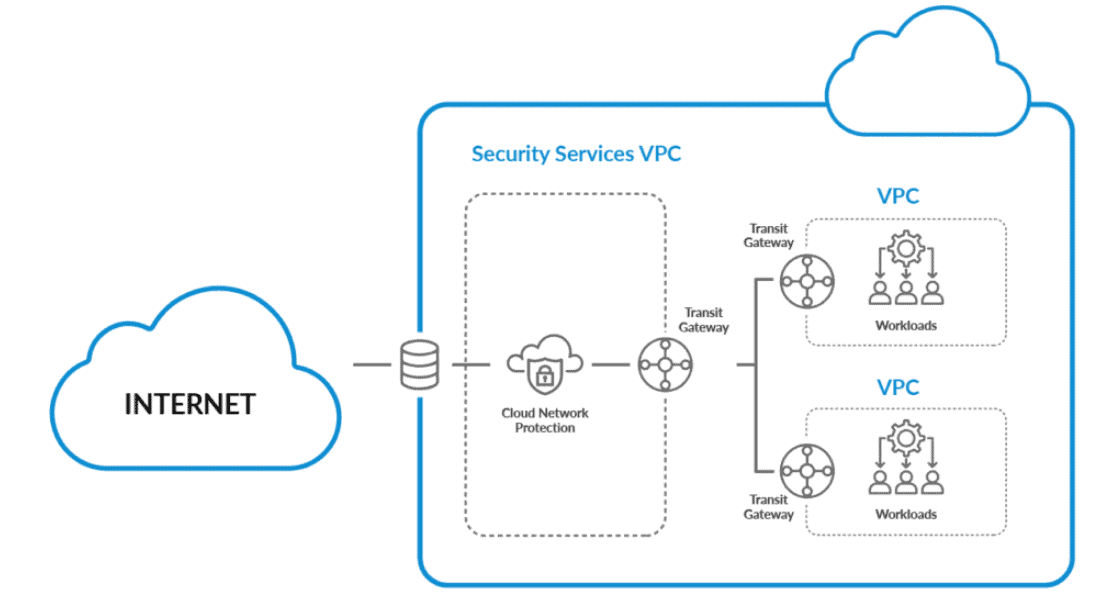
Click, to know more about Network Security
Q3. Can a private cloud also be hosted by an external provider?
Ans. Yes, it can be. Generally, a private cloud is hosted behind a company’s firewall. Alternatively, some businesses host their private cloud with a third-party provider, allowing them to access external computational resources on demand.
Application Security
Cloud application security is a set of policies, controls, and technologies that govern all data transfers in cloud collaboration environments like Microsoft Office 365, Slack, and Google G Suite. For example, you must have used cloud apps like those described above to store and exchange data (or any other available). To safeguard your application, a cloud application “safety net” must be included in your zero-trust security infrastructure.
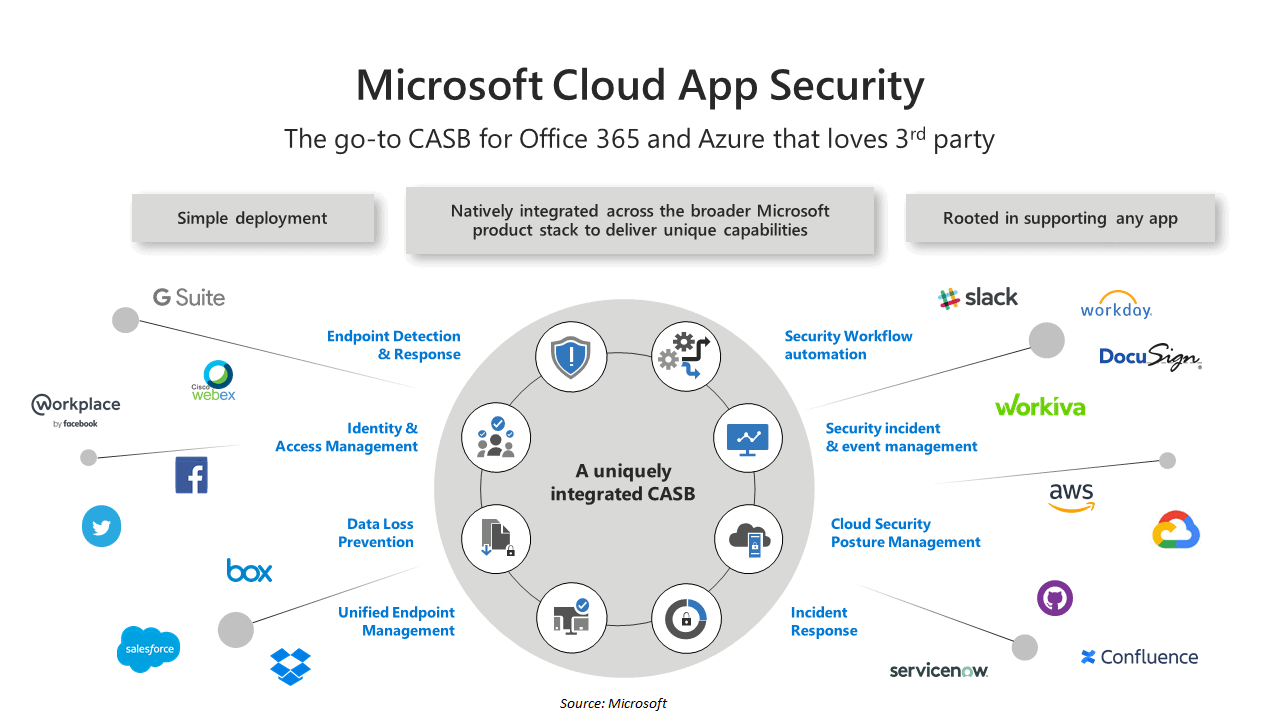
A widespread misunderstanding in the industry is that cloud apps must be safeguarded with the use of a proxy, browser extension, or other agents. On the other hand, Cloud security solutions are available that monitor, regulate, and secure behaviour within cloud apps using the native APIs of those apps. Two prominent choices on the market are an API and a proxy CASB.
Identity and Access Protection (IAM)
IAM is a security discipline that allows the appropriate individuals to access the appropriate resources at the appropriate times and for the appropriate purposes. IAM satisfies the mission-critical demand for ensuring proper resource access in increasingly diverse technical contexts.
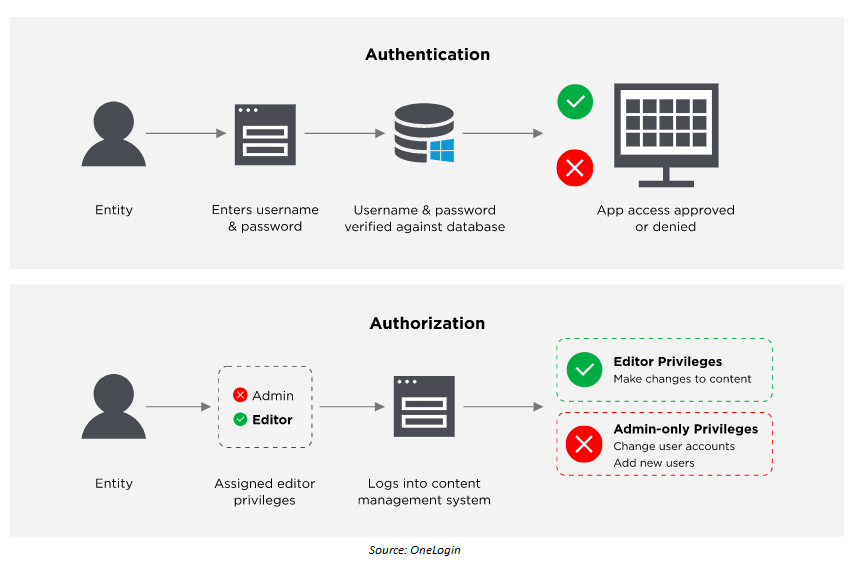
Also, learn about Active Directory from here
Q4. How does IAM protect a business from security breaches?
Ans. Identity and access management (IAM) is a security discipline that allows the right individuals to access the right resources at the right time for the right reasons. If two persons are working on two different projects, person one should not have access to the project of person two, and vice versa. We can set up roles so that unauthorized people can’t access the project and think negatively about it.
Database Security
Adapting to a cloud-centric infrastructure has many advantages in cost reductions, ease of setup, and time savings, but it also introduces new obstacles for IT teams. One of the most crucial is determining how to protect your cloud databases. Infrastructure and human resources go hand in hand with data security, compliance, and protection. The key is to have a robust database protection policy in place. To protect databases, you’ll require trained storage, system, and database administrators who are also familiar with data compliance rules.
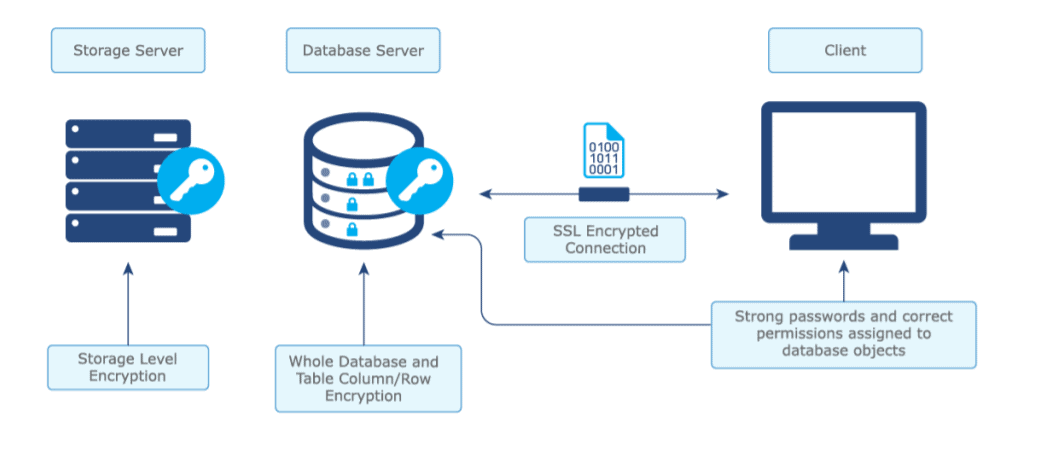
Q5. Suggest some steps to follow to secure your database in the cloud?
Ans. Some of the steps you can follow are:
- Data should be stored in multiple regions or zones.
- Use Virtual Private Cloud to run your database instances in logically isolated and private cloud environments.
- Use Secure Data Transfer
- Use Hybrid Cloud Architecture with Cloud Access Control
Container Security
A container is a software unit that wraps code and all of its dependencies, allowing it to be moved from one computing environment to another rapidly and reliably.
Q6. What are the most important considerations while securing containers?
Ans. Following are the most important consideration while securing containers.
- The container host’s security.
- Traffic on the container network.
- The container’s security for your application.
- Malicious activity within your program.
- Increasing the security of your container management stack.
- Your application’s fundamental layers. The build pipeline’s integrity.
Now that we’ve covered the fundamentals of all security concerns, we may move on. We’ll look at the various cloud security approaches we use, starting with the cloud responsibility model. Prior to that, I’d like you to gain a better understanding of what a traditional data centre is.
Traditional data centre
Traditionally, data centres are used to store information. In a typical data centre paradigm, you are responsible for security throughout your whole operating environment, including apps, physical servers, user controls, and even physical building security.
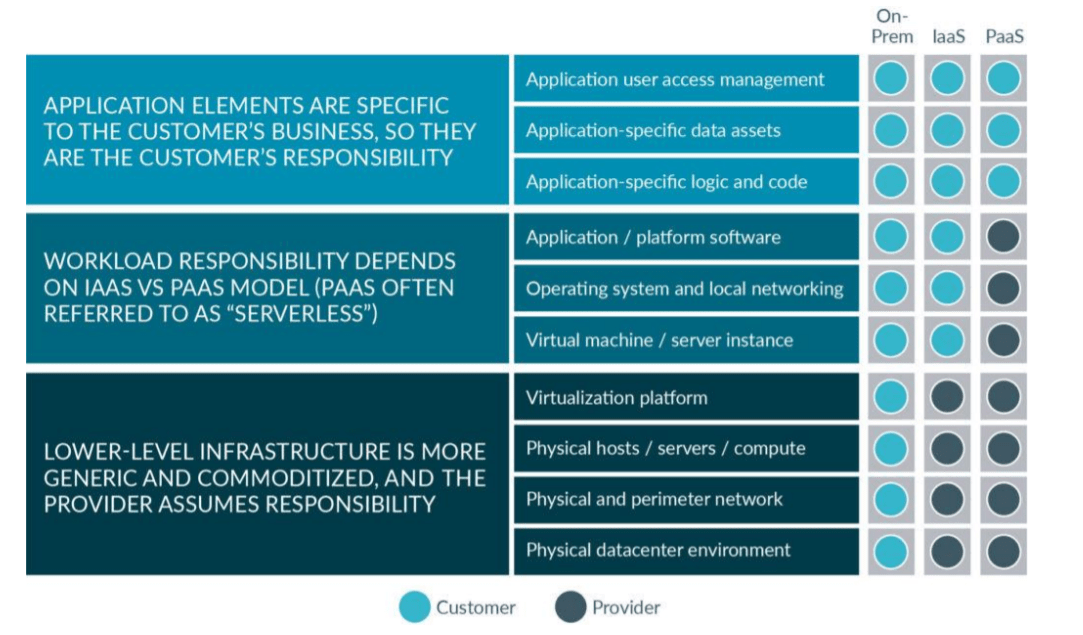
Cloud Security Responsibility Model
In the cloud environment, the Shared Responsibility Model is a concept. Your supplier relieves your team by taking on some of the operational tasks, such as security. In this shared responsibility model, security ownership must be expressed explicitly. By partnering with your cloud provider and sharing portions of the security responsibilities, you can maintain a safe environment with minimal operational overhead.
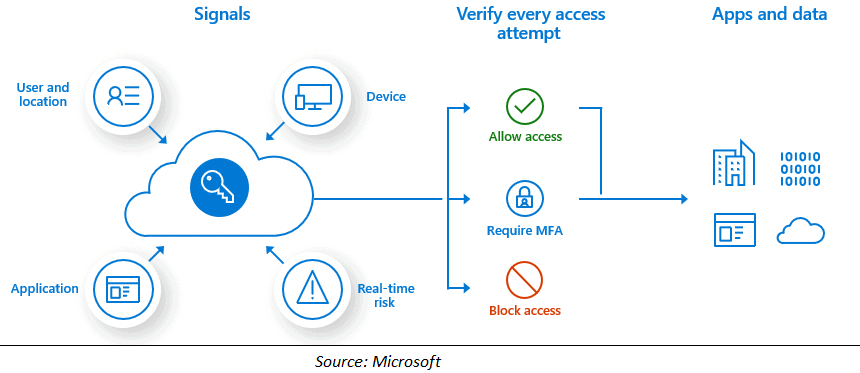
Zero Trust Model
A method of designing and implementing information technology systems is the zero-trust security model, often known as perimeter less security.

The Zero Trust model assumes a breach and evaluates each request as if it originated from an uncontrolled network, rather than presuming that everything behind the corporate firewall is safe. The Zero Trust paradigm pushes us to “never trust, always verify,” regardless of where the request originates or what resource it accesses. Zero Trust can be used by businesses to reduce cloud risk. Companies may improve their understanding of their users and devices, as well as their ability to detect threats and maintain network management.
Defense-In-Depth Model
Defense-in-depth is a security risk management strategy that defines many layers of security measures in an IT context. If one layer fails to detect a security compromise, the next is very certainly going to catch it. The numerous layers improve the environment’s overall security score and considerably lower the risk of a security breach.
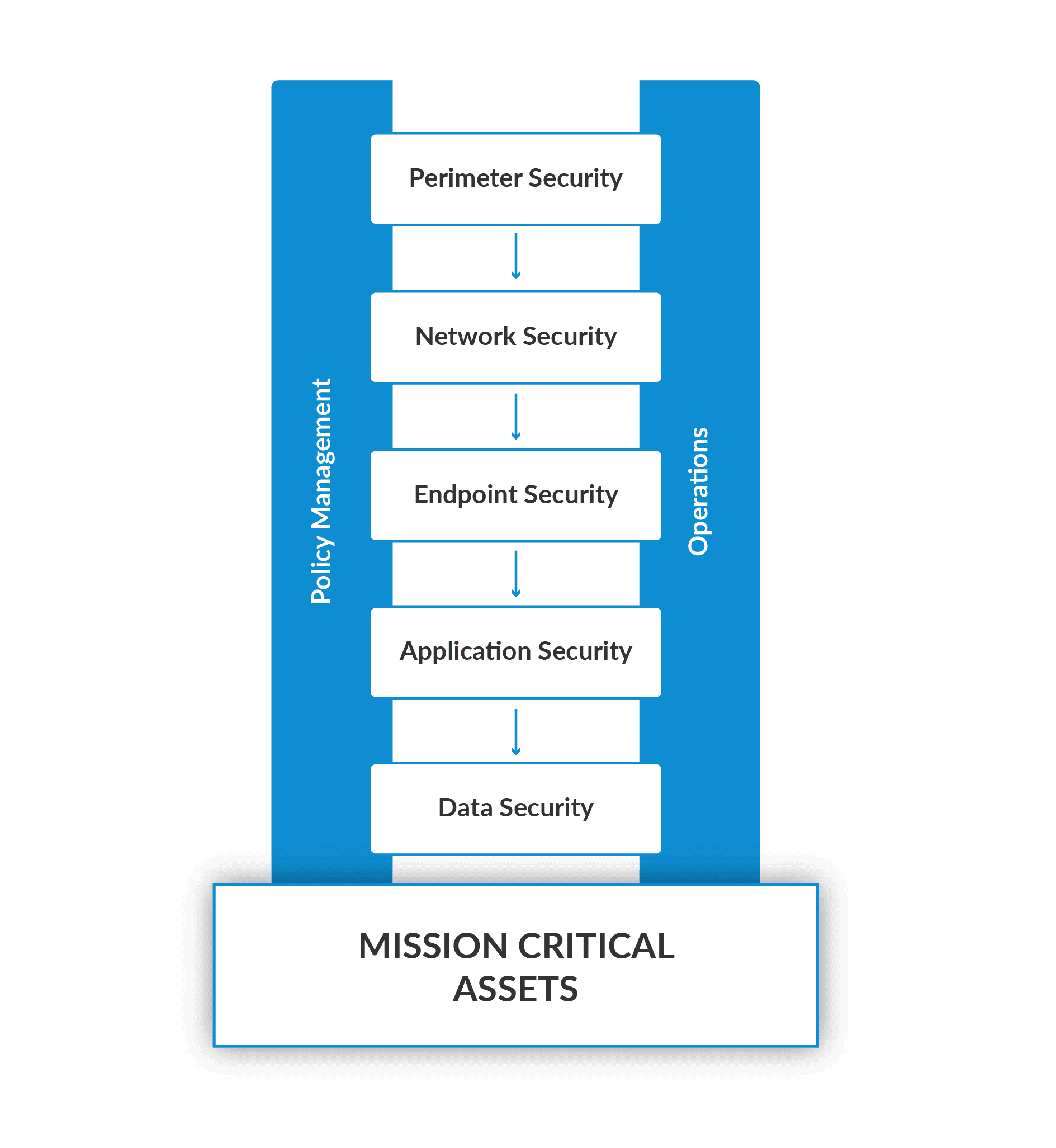
Q7. What are the different layers of Defense-In-Depth?
Ans. Security in the cloud is a shared responsibility. Each security layer is either the cloud provider’s or the customer’s responsibility. In the case of Azure:
- Physical Security: Microsoft is the owner of the Azure data centres and is in charge of physical security at all of them.
- Identity and Access: Azure Active Directory governs and controls all Azure resources.
- Perimeter: Basic Distributed Denial of Service (DDoS) security is enabled by default in Azure, which includes always-on traffic monitoring and real-time mitigation of typical network-level assaults.
- Network: Network Security Groups, which contain security rules allowing or forbidding traffic, can be used to filter network traffic to and from Azure resources in a virtual network.
- Compute: The Azure Security Center’s capacity to process signals and detect security threats such as RDP brute-force attacks and SQL injections gives protection against threats.
- Application: Web Application Firewalls and Application Gateways provide centralized security for your web applications against typical attacks and vulnerabilities.
- Data: Both unstructured and structured data are encrypted at rest.
Cloud-First Strategies
Cloud-first strategies are operational approaches in which organizations move all or most of their infrastructure to cloud computing platforms like Amazon Web Services, Google Cloud, Microsoft Azure, or Oracle.
The six-point strategy:
- Assessment phase: In this step, you evaluate the cost, architecture, and security implications of a cloud-first strategy.
- Proof of Concept Phase: This step involves developing and implementing a cloud-first strategy in your firm.
- Data Migration Phase: You make use of the various data storage alternatives accessible to choose the best security solution that fits your budget.
- Application Migration Phase: You must choose the form of migration to which your company will adapt.
- Leveraging the Cloud Phase: You use the capabilities and flexibility provided by cloud space to auto scale and automate your functions at this point.
- Optimization phase: The optimization phase is where you tune and improve the system to ensure that it is making the best use of available resources
Multi-Factor Authentication
Multi-factor authentication is when a user must provide two or more pieces of evidence to confirm their identity in order to gain access to an app or digital resource. MFA (multi-factor authentication) is a security solution that ensures digital users are who they say they are.

Cloud Monitoring Solution
The practice of assessing, monitoring, and managing operational activities in a cloud-based IT infrastructure is known as cloud monitoring. To check the availability and performance of websites, servers, applications, and other cloud infrastructure, manual and automated management methodologies are utilized. This ongoing assessment of resource levels, server response times, and performance points to future threats as a potential risk.
Leading Cloud Service Providers In the Market

- AWS is the cloud services industry’s oldest, most mature, and regularly active player
- Microsoft Azure takes a customer-centric approach that prioritizes compatibility and efficiency.
- When it comes to cloud data and security, Google is a well-established organization.
- Oracle Cloud Infrastructure optimizes analytics and transaction processing workloads for Autonomous databases.
Quiz Time (Sample Exam Questions)!
With our Cloud Security For Azure, AWS, Google Cloud & Oracle training program, we cover 220+ sample exam questions to help you prepare for the certification like AZ-500.
Check out one of the questions and see if you can crack this…
Ques: Your Company is planning to move to the cloud, and your biggest concern is security. Which cloud security approach you will adopt to meet security demand?
A. Shared Responsibility Model
B. Defense-In-Depth Model
C. Cloud-First Strategies
D. Multi-Factor Authentication.
The right answer will be revealed in my next week’s blog.
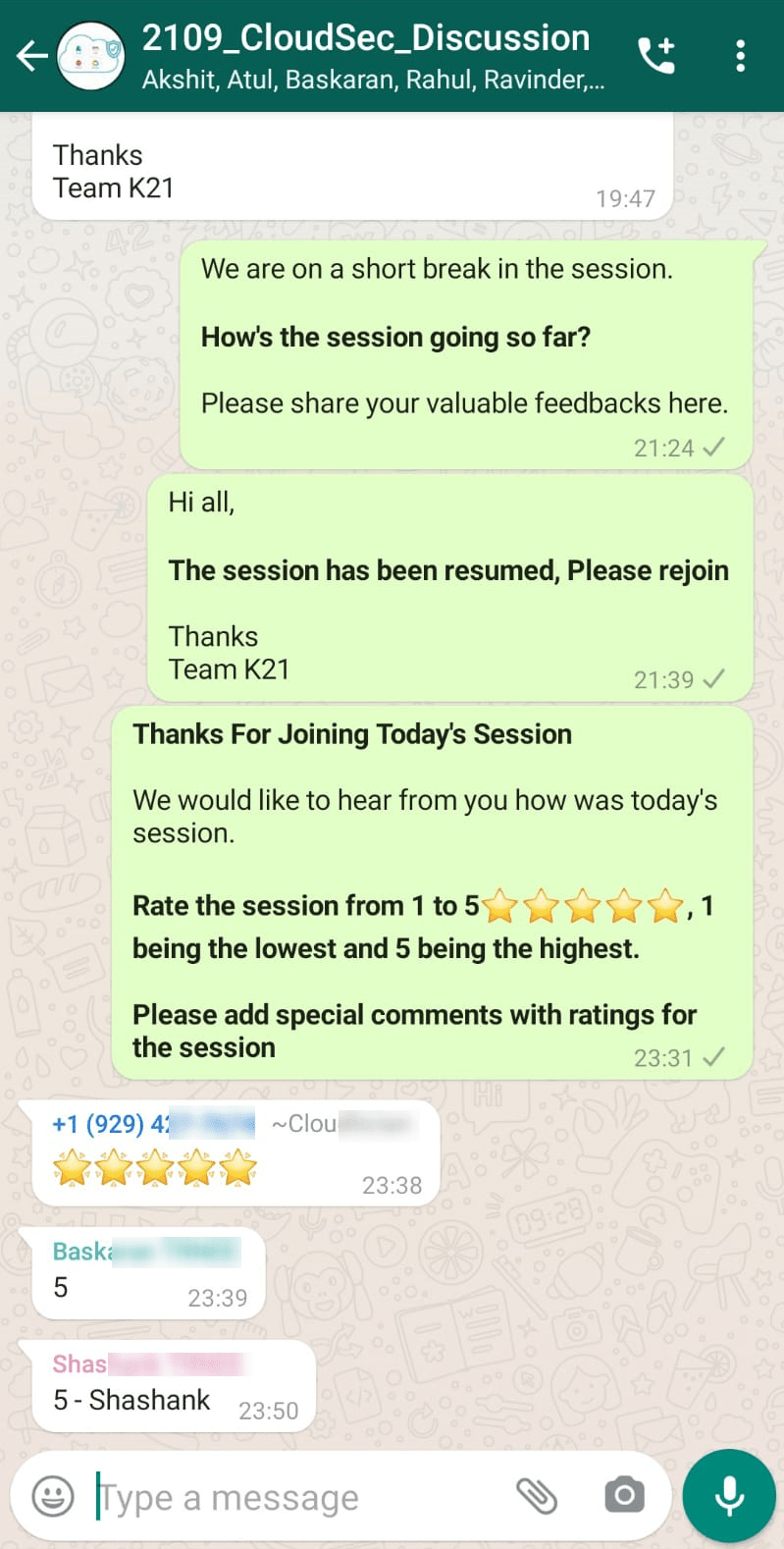
Feedback
We always work on improving and being the best version of ourselves from previous sessions; hence constantly ask for feedback from our attendees.
Here’s the feedback that we received from our trainees who had attended the session…
Related/References
-
- Microsoft Azure Secure Network Connectivity: Firewall, DDOS, & NSG
- Microsoft Azure Security Technologies: Step By Step Activity Guides
- Microsoft Azure Security Technologies Certification
- Azure Security Center [AZ-500]: Everything You Should Know
- Top 10 best practices for Azure Security in 2021
- [AZ-500] All about Azure Active Directory
- Azure Firewall vs Azure Network Security Groups (NSG)
- Azure Firewall: Overview and Concepts
Next Task For You
To get more clarity on what to expect in the training program, I recommend you to attend the FREE Class I’m holding this weekend! This FREE class will help you to understand what the training program looks like and give will you a clear vision to plan your career ahead!
Join me in the FREE Session and fast track your success!
Click on the below image and Register for our FREE CLASS Now!



![Microsoft Agentic AI Business Solutions Architect [AB-100] | K21 Academy](https://test.k21academy.com/wp-content/uploads/2025/11/Microsoft-Agentic-AI-Business-Solutions-Architect-AB-100-Exam-Overview1.png)


