![]()
This blog post gives a walkthrough of the Step-By-Step Activity Guides of the AWS Certified Security – Specialty (SCS-C02) training program that you must perform to learn this course.
The walkthrough of the Step-By-Step Activity Guides of AWS Certified Security – Specialty (SCS-C02) training program will prepare you thoroughly for the AWS SCS-C02 certification and apply for the exam click here.
List of Labs that we include in Our training AWS Certified Security – Specialty (SCS-C02)
- Create AWS Free Trial Account
- Create IAM users, groups, roles & Policies
- Create a Power user
- Enable MFA on the root account
- Create a user pool in AWS Cognito
- Working AWS Organizations & Service Control Policies
- Working with Simple AD
- Understanding Lambda@Edge
- Setting Up AWS Config to Assess Audit & Evaluate AWS Resources
- Enable CloudTrail and Store Logs in S3
- Install CloudWatch Agent on EC2 Instance & View CloudWatch Metrics
- AWS Access control alerts with CloudWatch & CloudTrail.
- Check AWS Resources in Trusted Advisor
- Check the Compliance status of the Security group
- Classify sensitive data in your environment using Amazon Macie
- Registering a Domain Name For Free
- Working with Route53 for Disaster Recovery
- Block web traffic with WAF
- Find vulnerabilities on an EC2 instance using Amazon Inspector
- Get started with Amazon ECS using Fargate
- Understanding & Configuring Layered Security in an AWS VPC
- Understanding Stateful vs Stateless Firewalls
- How to set up an AWS Site-to-Site (S2S) VPN Connection
- How to implement end to end VPC Endpoint service
- Access EC2 from Session manager & send SSH logs to CloudWatch
- Using AWS Systems Manager for Patch Management
- Implementing AWS WAF with ALB to block SQL Injection, Geo-Location & Query string
Activity Guide I: Create AWS Free Trial Account
Amazon Web Services (AWS) is continuously providing 12 months of Free Tier account to new subscribers to get hands-on experience with all the AWS cloud services. In this AWS Free Tier account, Amazon is giving the number of different services used with some of the limitations to get hands-on practice and more knowledge on AWS Cloud services as well as regular business use.
Check out our blog on How To Create AWS Free Tier Account for more information.

In this activity guide, you will learn how to register for an AWS Free Tier account and logging into AWS Console
Activity Guide II: Create IAM Users, Groups, Roles & Policies
AWS Identity and Access Management is a service provided by AWS that helps you to securely control the access to AWS resources. You can use the IAM service to control the user, who is authenticated (signed in) and authorized (has permissions) to use service/resources.
When you first create an AWS account and you begin with a single sign-in identity that has complete access to all AWS services/resources in the account. This identity is called the AWS Root user and is accessed by signing in with the email and password that you used to create the account. Here we strongly recommend you do not use the root user for your daily tasks, even the administrative ones. Instead, adhere to the best practice of using your root user only to create the IAM user and for billing purposes only and then securely lock away your root account credentials and use that account to perform only a few service management tasks.
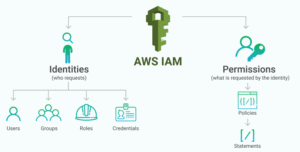
In this activity guide, You will learn how to use create an IAM user, role, Group and attach policies to it.
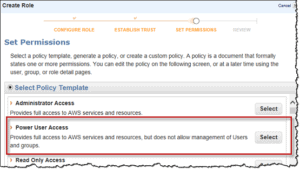
Activity Guide III: Create a Power User
The Power User is the IAM user who has full access to the AWS services and resources but does not allow management of IAM Users and IAM groups. The power to manage users is the highest privilege operation in AWS thus it is provided to the administrative access policy only. Power-user is just one step below the admin access and who has all the privileges but does not have the ability to manage IAM users.
In this activity guide, You will learn how to create an IAM power user and for what kind of services he is authorized.
Activity Guide IV: Enable MFA on The Root Account
AWS Multi-Factor Authentication is a simple best practice that adds an additional layer of protection on the top of your user name and password. With the enabled MFA, when a user signs in to an AWS Console, they will be prompted for their user name and password (First authentication), as well as for an authentication code (Second Authentication) from their AWS MFA device. These details are Taken together to increase security for your AWS account settings and resources.
You can enable MFA for your AWS account as well as for an individual IAM user you have created under your root account. MFA is also used to control access to AWS service APIs. AWS does not charge any additional cost for using the MFA.
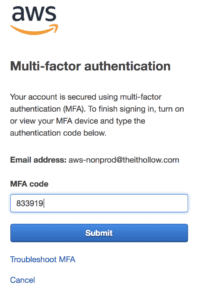
In this activity guide, You will learn how to use enable the MFA on your root account.
Activity Guide V: Create a User Pool in AWS Cognito
A user pool is a user directory in Amazon Cognito. With a user pool, users can sign in to your web or mobile app through Amazon Cognito. Whether your users sign indirectly or through a third party, all members of the user pool have a directory profile that you can access through a Software Development Kit (SDK).
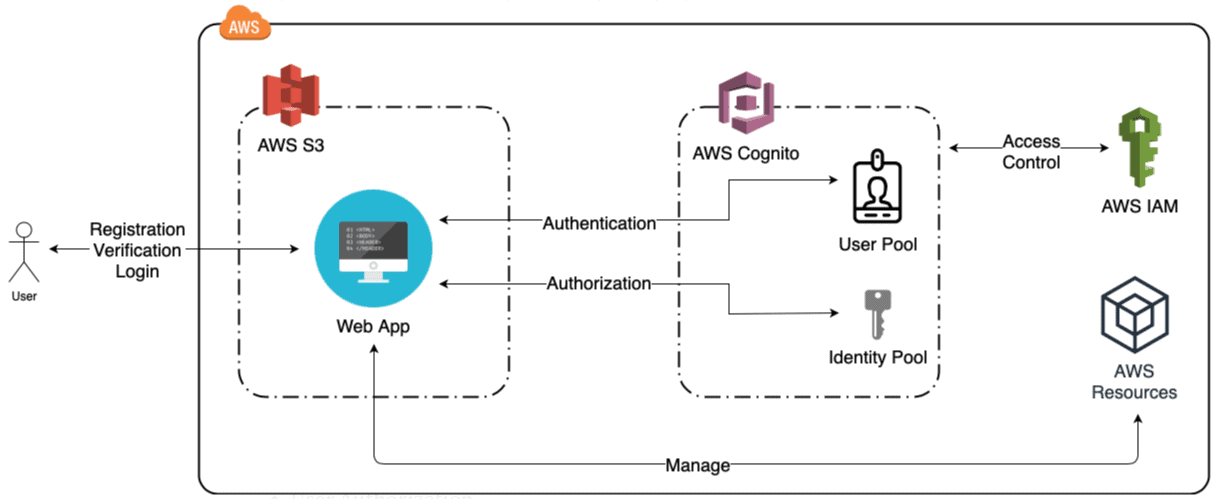 In this activity guide, you will learn how to create a user pool in AWS Cognito.
In this activity guide, you will learn how to create a user pool in AWS Cognito.
Activity Guide VI: Working AWS Organizations & Service Control Policies
AWS Organizations helps you centrally govern your environment as you grow and scale your workloads on AWS. Whether you are a growing startup or a large enterprise, Organizations help you to centrally manage to bill; control access, compliance, and security; and share resources across your AWS accounts.
Using AWS Organizations, you can automate account creation, create groups of accounts to reflect your business needs, and apply policies for these groups for governance. You can also simplify billing by setting up a single payment method for all of your AWS accounts.
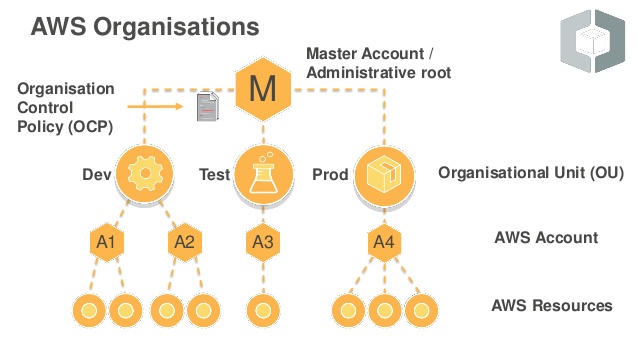
In this activity guide, you will learn to create and manage AWS Organizations using SCP (Service Control Policies).
Activity Guide VII: Working With Simple AD
Amazon Directory Service provides different ways to use Microsoft Active Directory (AD) with other AWS services. These Directories store information about users, groups, and devices, and administrators use them to manage access to information and resources.
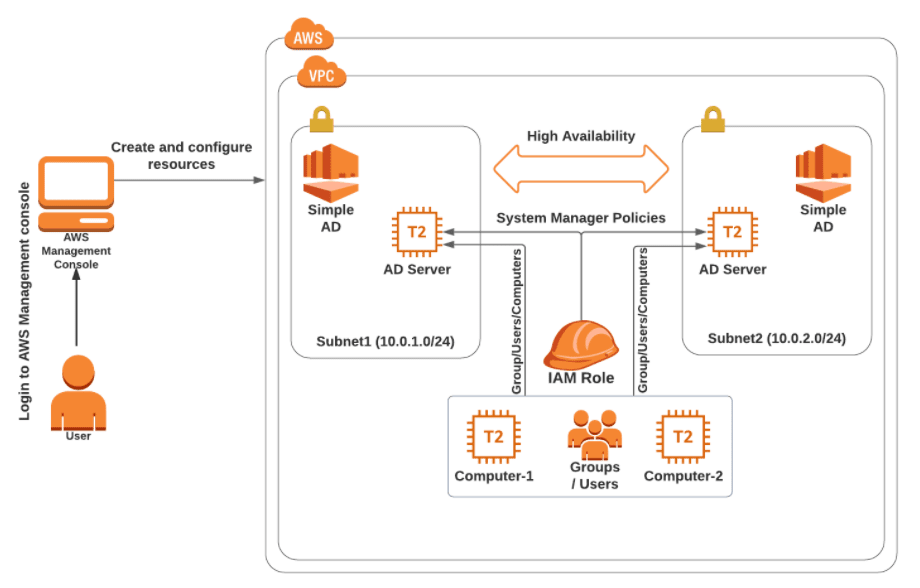
In this Activity guide, you will learn how to create a Simple AD directory, add Groups, Users and Computers.
Activity Guide VIII: Understanding Lambda@Edge
Lambda@Edge is a feature of CloudFront that allows you to run the code closer to users of your application, which improves performance & reduces latency.
Lambda@Edge runs the code in response to events generated by the CloudFront content delivery network (CDN). Just upload the code to Lambda, run and scale your code with HA at an AWS location closest to your end-user. There are no servers to manage & you can customize your content delivery.
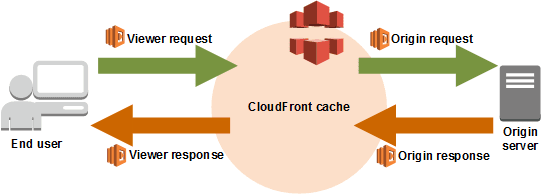
In this activity guide, you will learn about how we are implementing Lambda@edge at origin request. The lambda will be redirecting the path to the appropriate HTML page based on the user URL.
Activity Guide IX: Setting Up AWS Config to Assess Audit & Evaluate AWS Resources
AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. With Config, you can review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines.
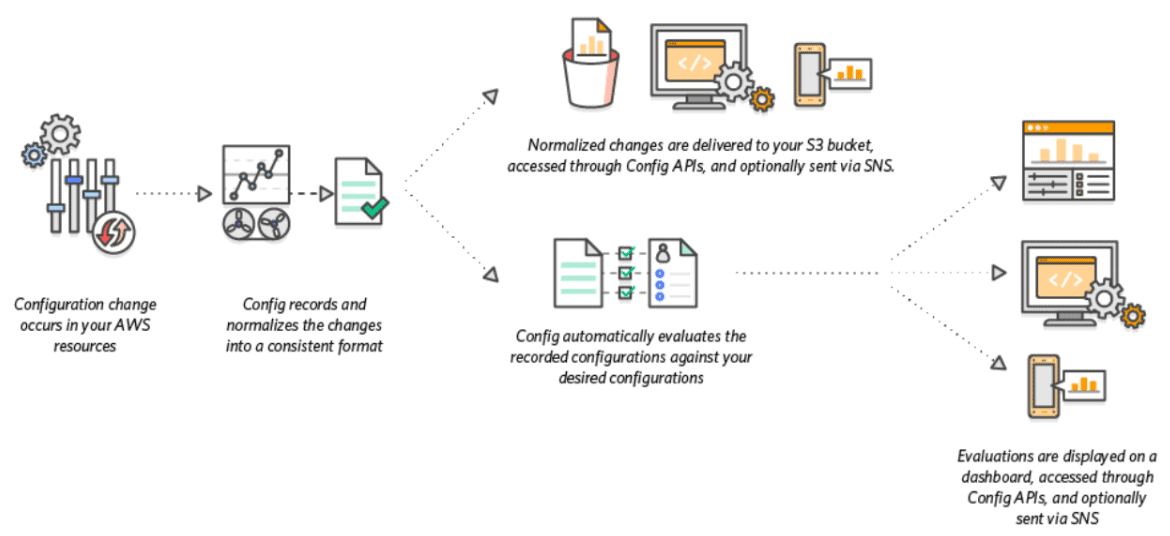
In this activity guide, you will learn how to Enabling Governance using AWS Config
Activity Guide X: Enable CloudTrail & Store Logs in S3
Amazon S3 is integrated with AWS CloudTrail, a service that provides a record of actions taken by a user, role, or an AWS service in Amazon S3. CloudTrail captures a subset of API calls for Amazon S3 as events, including calls from the Amazon S3 console and from code calls to the Amazon S3 APIs.
If you create a trail, you can enable continuous delivery of CloudTrail events to an Amazon S3 bucket, including events for Amazon S3.

In this activity guide, you will learn to implement step-by-step instructions to create a trail and store logs in an S3 bucket.
Activity Guide XI: Install CloudWatch Agent on EC2 Instance & View CloudWatch Metrics
Amazon CloudWatch is a monitoring and observability service built for DevOps engineers, developers, site reliability engineers (SREs), and IT managers. CloudWatch provides you with data and actionable insights to monitor your applications, respond to system-wide performance changes, optimize resource utilization, and get a unified view of operational health.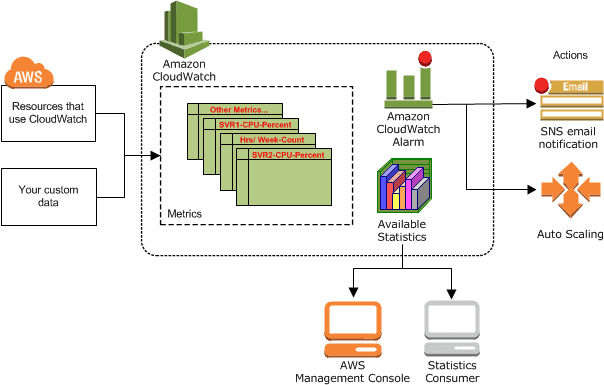
In this activity guide, we cover Step by step instructions for installing CloudWatch Agent on EC2 instance for Metrics Visualization
Activity Guide XII: AWS Access Control Alerts With CloudWatch & CloudTrail
Amazon Cloudwatch is the service that is used to monitor and collect the metrics from services periodically. You can use CloudWatch to detect anomalous behaviour in your environments & to set an alarm, You can visualize data from the logs & take actions to troubleshoot the issue.
AWS CloudTrail is a service that helps us monitor, survey, and audit our AWS Account. With the help of AWS CloudTrail, the user will be able to log, monitor, and retain account activity associated with actions across the AWS infrastructure.

In this activity guide, you will learn how to create a Cloudtrail and CloudWatch log group, while also creating a metric filter to receive an alarm from CloudWatch via SNS topic.
Activity Guide XIII: Check AWS Resources in Trusted Advisor
AWS Trusted Advisors provides the recommendations that help you to follow the best practices. The Trusted Advisor evaluates your account by using checks. These checks can identify ways to optimize your infrastructure, improve security & performance, reduce costs, & monitor service quotas.
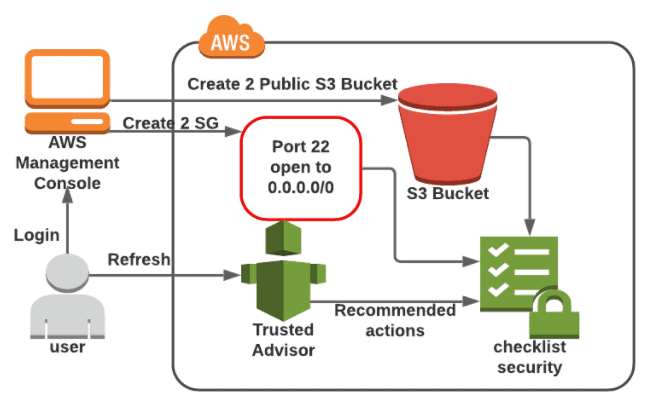
In this Activity Guide, you will learn how to monitor the Unrestricted Security group and public S3 Bucket with the help of AWS Trusted Advisor.
Activity Guide XIV: Check The Compliance Status of The Security Group
AWS Config comes under the Management & Governance category in the list of present categories and services. Config takes care of an audit, evaluation, and assessment of AWS Resources in your account.
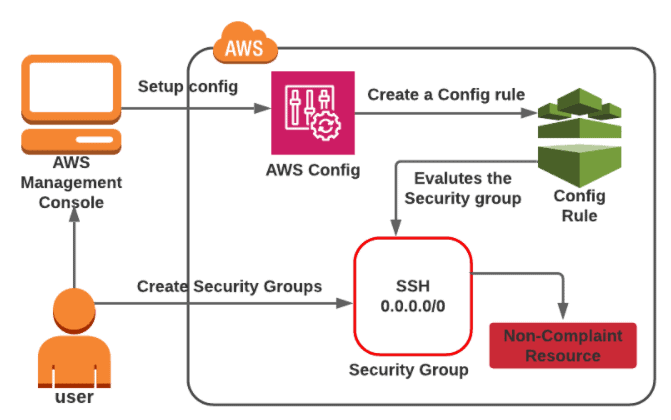
In this Activity guide, you will learn how to set up a recording configuration setting for AWS Config and Detect the unprotected Security groups present in the account.
Activity Guide XV: Classify Sensitive Data in Your Environment Using Amazon Macie
Amazon Macie uses machine learning and pattern matching to cost-efficiently discover sensitive data at scale. Macie automatically detects a large and growing list of sensitive data types, including personally identifiable information (PII) such as names, addresses, and credit card numbers.
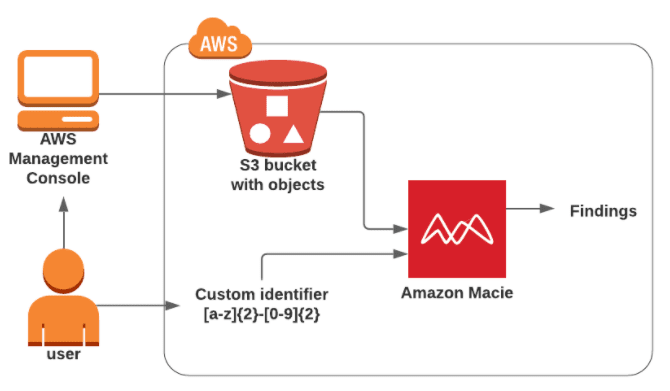
In this activity guide, you will learn how to create and configure an Amazon Macie job to discover sensitive data.
Activity Guide XVI: Registering a Domain Name For Free
All computers on the Internet, from your smartphone, laptop/PC to the servers that serve content for massive retail websites, can be found and communicate with one another by using numbers. These numbers are called IP addresses. When you go visit a website through your browser, you don’t have to remember and enter a long number. Instead, you can enter a DNS name (domain) like example.com.
In this activity guide, you will learn how to get a domain name for free.
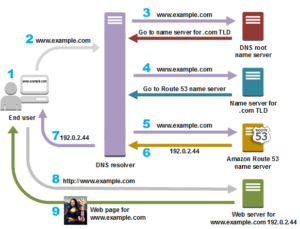
Activity Guide XVII: Working with Route53 for Disaster Recovery
Amazon Route 53 is a highly available and scalable cloud Domain Name System (DNS) web service. It is designed to give developers and businesses an extremely reliable and cost-effective way to route end users to Internet applications by translating names like www.example.com into the numeric IP addresses like 192.0.2.1 that computers use to connect. Amazon Route 53 is fully compliant with IPv6 as well.

In this activity guide, you will learn how to plan the recovery from a disaster using Route53, Active-Active Failovers, and Active-Passive Failovers.
Activity Guide XVIII: Block Web Traffic with WAF
AWS Web Application Firewall is a firewall that helps you to protect your web application server against common web exploits that might affect the availability and compromise the security concerns of your application. The AWS WAF also gives you control over the traffic that it reaches to your applications by enabling you to create security rules that block common attack patterns like SQL injection and cross-site scripting.
The Users can create their own rules/policies and specify the conditions that AWS WAF searches for in incoming web requests, and the AWS cost for using the WAF is only for what you use.
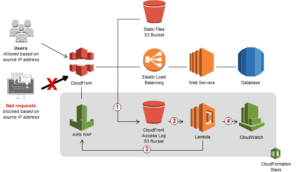
In this activity guide, you will learn how to create an IP set and test the working of WAF.
Activity Guide XIX: Find Vulnerabilities on an EC2 Instance Using Amazon Inspector
Amazon Inspector tests the network accessibility of your Amazon EC2 instances and the security state of your applications that run on those instances. Amazon Inspector assesses applications for exposure, vulnerabilities, and deviations from best practices. After performing an assessment, Amazon Inspector produces a detailed list of security findings that is organized by level of severity.
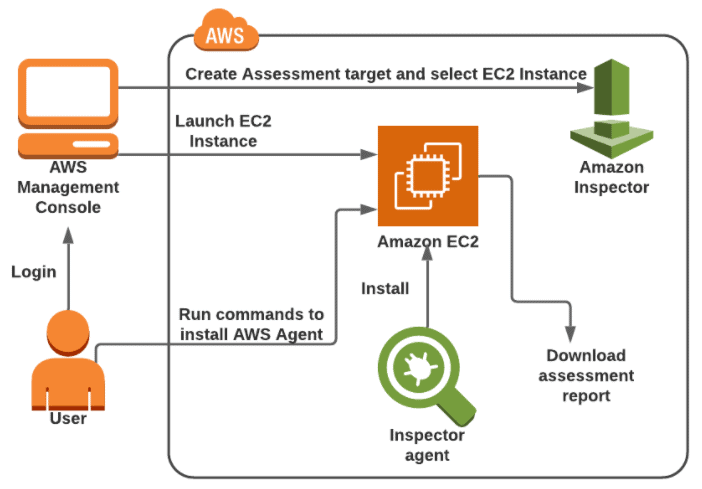
In this Activity guide, you will learn how to launch the EC2 instance and configure an Inspector with an Assessment target and template.
Activity Guide XX: Get Started with Amazon ECS Using Fargate
AWS Fargate is a technology that you can use with Amazon ECS to run containers without the overhead of managing servers or clusters of instances. With Fargate, and no longer need to have provisioned, configured, or scale the clusters of virtual machines to run containers. This removes the need to choose server types, decide when to scale your clusters or optimize cluster packing.
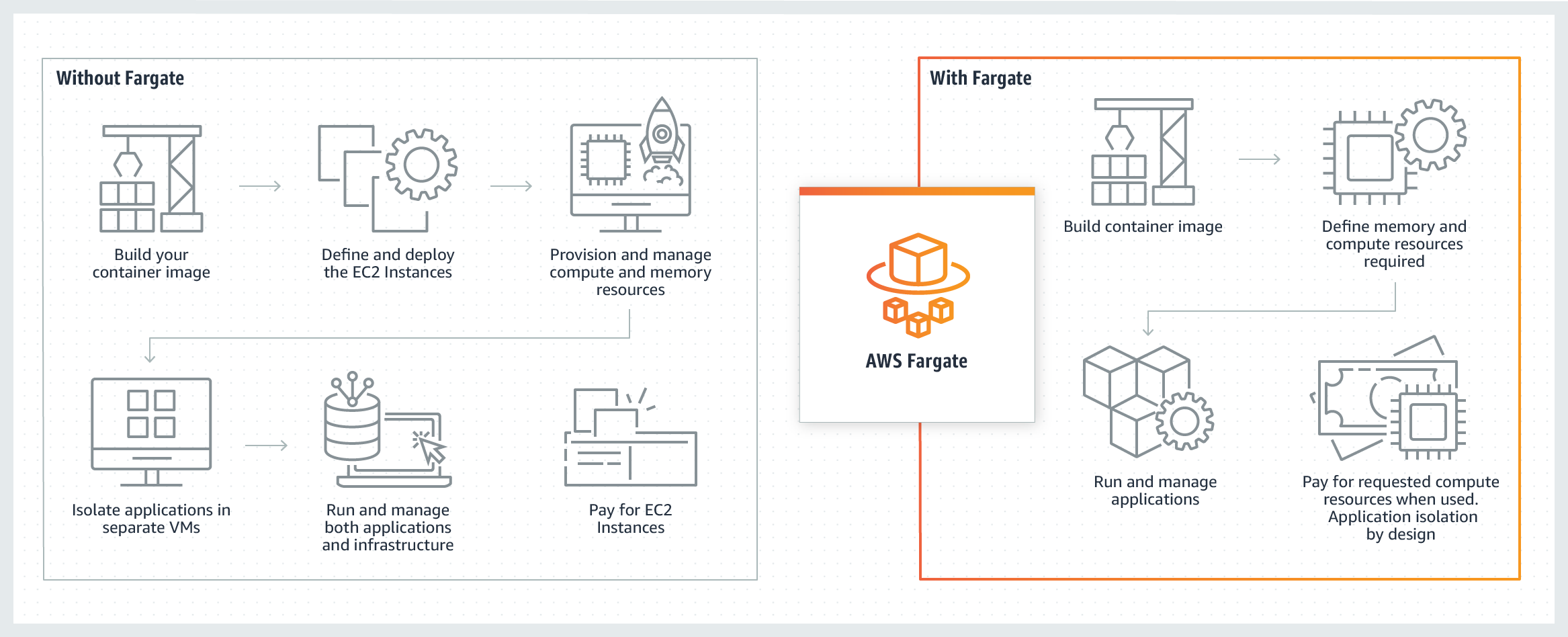
In this Activity guide, you will learn about ECS using the fargate launch type.
Activity Guide XXI: Understanding & Configuring Layered Security in an AWS VPC
Amazon VPC allows you to launch your AWS resources in an isolated network that is defined by us in a more private & secure way. This feature enables us to increase the security level of the AWS resources.
The AWS resources can be protected using multilayered VPC which includes security groups and a Network Access Control List. The VPC security group provides security at the instance level which acts as a firewall and controls both inbound and outbound traffic.
The VPC NACL provides security at Network Level i.e subnet level which acts as a firewall for associated subnets and controls inbound and outbound traffic.
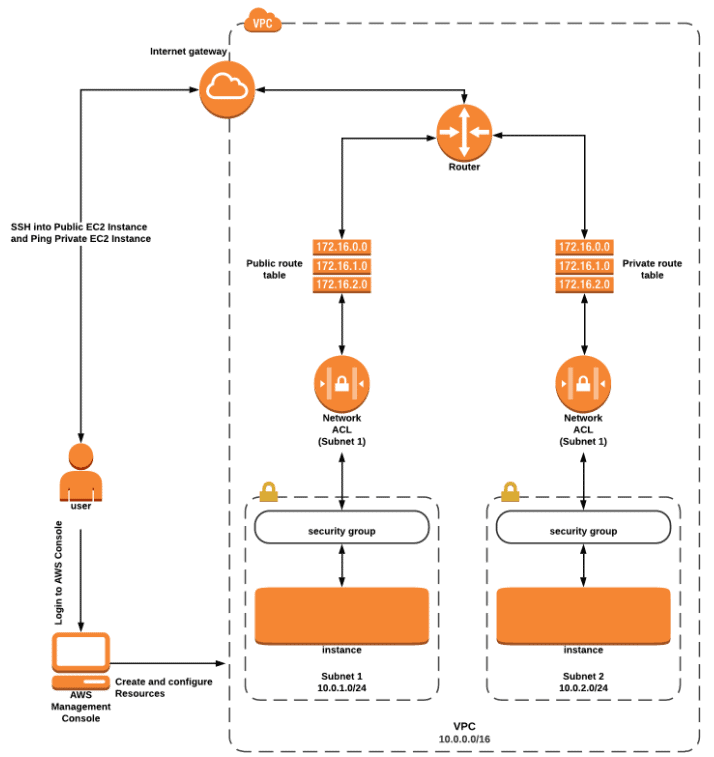
In this Activity Guide, you will learn how to configure Multi-layered Security in AWS VPC and launch 2 EC2 instances (one in a public subnet and another in a private subnet)
Activity Guide XXII: Understanding Stateful vs Stateless Firewalls
Security groups are stateful: This means any changes applied to an incoming rule will be automatically applied to the outgoing rule. If you allow an incoming port 22, the outgoing port 22 will be automatically opened.
Network ACLs are stateless: This means any changes applied to an incoming rule will not be applied to the outgoing rule. If you allow an incoming port 22, you would also need to apply the rule for outgoing traffic.
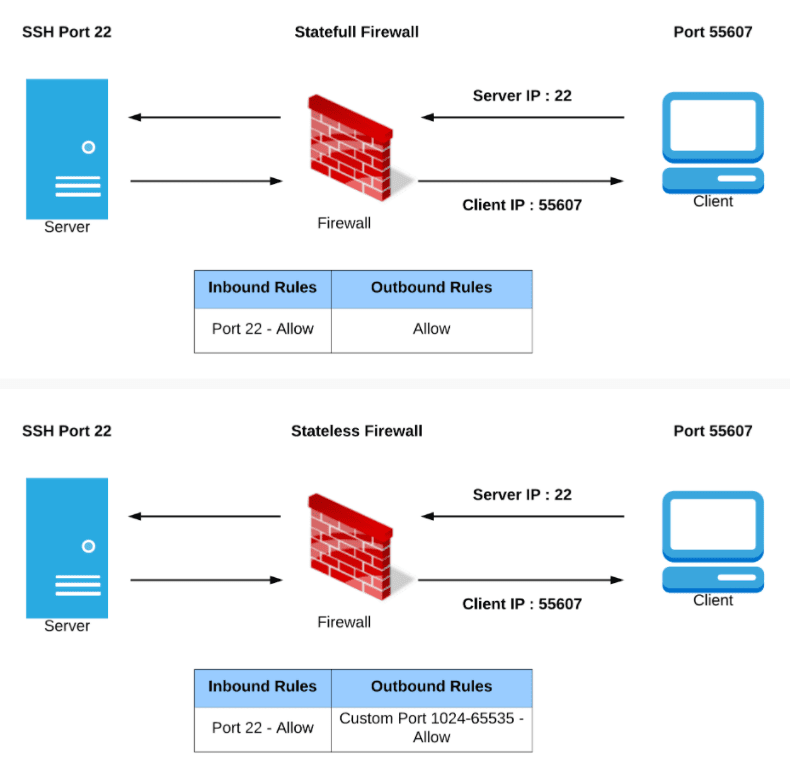
In this Activity Guide, you will understand the difference between stateful (Security group) and stateless (Network ACL) firewalls.
Activity Guide XXIII: How to Set Up an AWS Site-to-Site (S2S) VPN Connection
A VPN connection means the connection is between your VPC & your on-premises network. Site-to-Site VPN supports the Internet Protocol security (IPsec) VPN connections. By default, the resources that you create/launch into an Amazon VPC can’t communicate to each other with your own (remote/ on-premises) network.
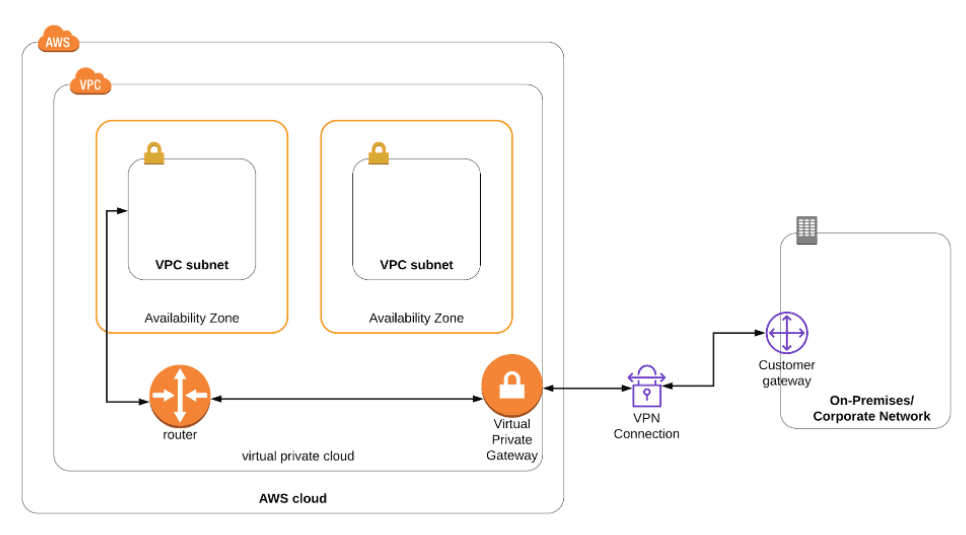
In this Activity Guide, you will how to set up a site to site VPN connection between your AWS Cloud and On-premise Network.
Activity Guide XXIV: How to Implement End to End VPC Endpoint Service
A VPC endpoint enables you a connection between a virtual private cloud (VPC) and support services, without an internet gateway, NAT device, VPN connection, or AWS Direct Connect. Therefore, your VPC is not exposed to the public.
VPC endpoints are virtual devices. They are horizontally scaled, redundant, & highly available VPC components.
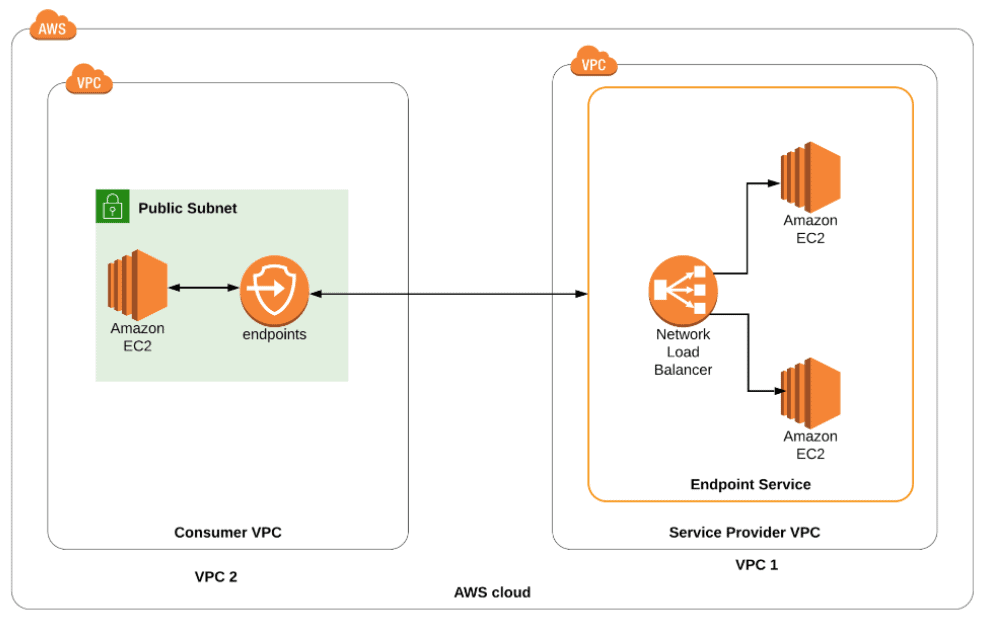
In this Activity Guide, you learn how to set up an end to end connection between two VPC’s (Services Provider and customer) using Endpoint service
Activity Guide XXV: Access EC2 From Session Manager & Send SSH Logs to CloudWatch
Session Manager is a fully managed AWS Systems Manager capability that lets you manage your Amazon Elastic Compute Cloud (Amazon EC2) instances, on-premises instances, and virtual machines (VMs) through an interactive one-click browser-based shell or through the AWS Command Line Interface (AWS CLI). Session Manager provides secure and auditable instance management without the need to open inbound ports, maintain bastion hosts, or manage SSH keys.
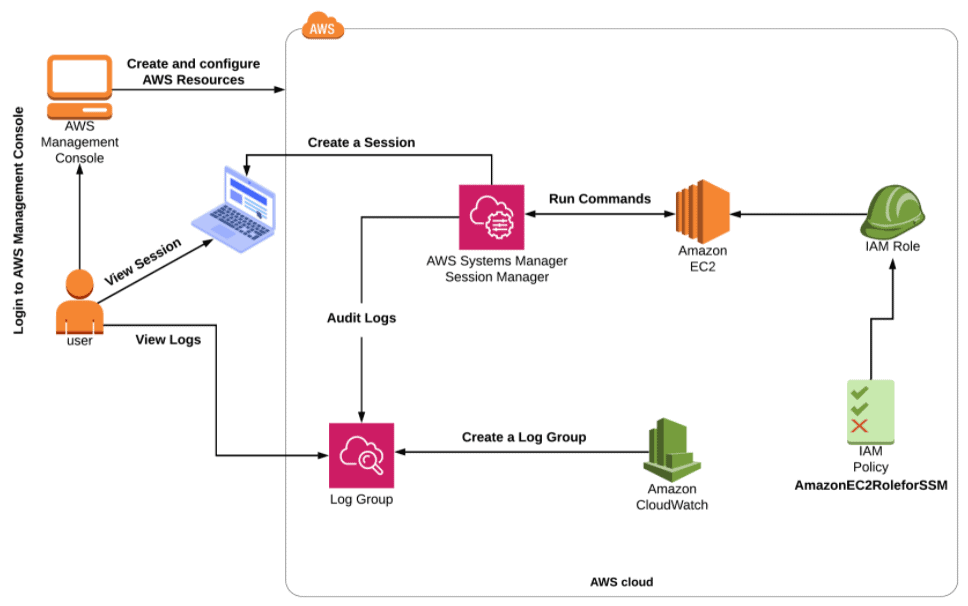
In this Activity Guide, you will learn how to launch an EC2 instance with the SSM role and then connect to the EC2 via AWS Session manager and view the logs in Cloudwatch.
Activity Guide XXVI: Using AWS Systems Manager For Patch Management
AWS Systems Manager gives you visibility and control of your infrastructure on AWS. Systems Manager provides a unified user interface so you can view operational data from multiple AWS services and allows you to automate operational tasks across your AWS resources.

In this activity guide, you will learn the creation and management of Infrastructure using AWS SSM.
Activity Guide XXVII: Implementing AWS WAF With ALB to Block SQL Injection, Geo-Location & Query string
Amazon WAF is a web application firewall that helps you to secure your web applications against common web exploits that might affect availability & compromise the security of your application. WAF gives you control over how traffic reaches your application server by enabling you to create rules that block common attack patterns like SQL injection & cross-site scripting. It allows the request to reach the application server based on the rules or patterns you define.
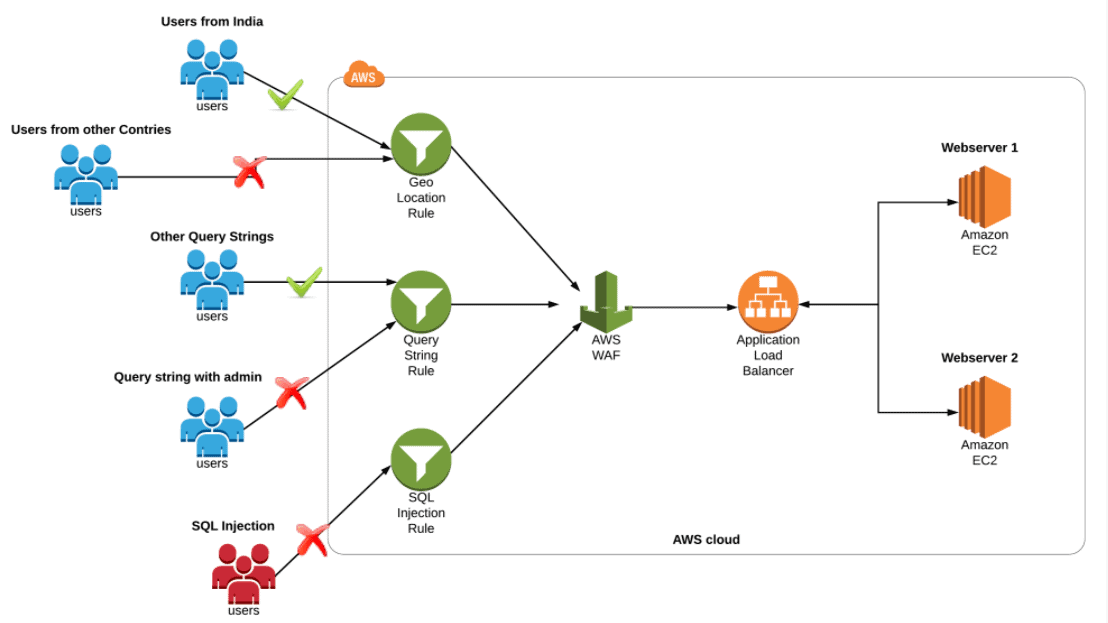
In this Activity Guide, you will learn how to set up WAF and create a set of rules to block access from geo-locations, SQL Injections and block certain Query String parameters.
Related References
- AWS Certificate Manager: Overview, Features and How it Works?
- AWS Database Services – Amazon RDS, Aurora, DynamoDB, ElastiCache
- Multi-Account Management Using AWS Organizations
- AWS Certified Solutions Architect: Roles & Responsibilities
- Amazon Kinesis Overview, Features And Benefits
- AWS Route 53 Introduction
Next Task For You
Begin your journey towards an AWS Cloud by joining our FREE Informative Class on Amazon Cloud Free Class by clicking on the below image.






![Microsoft Agentic AI Business Solutions Architect [AB-100] | K21 Academy](https://test.k21academy.com/wp-content/uploads/2025/11/Microsoft-Agentic-AI-Business-Solutions-Architect-AB-100-Exam-Overview1.png)



