![]()
“The cloud has evolved as a powerful force, altering the way we store, process, and access data amid the ever expanding horizons of digital change. But this technological marvel also raises a serious issue with Cloud Security.”
This blog post covers everything you need to know about the Cloud Security(AWS/Azure) with DevSecOps.
You can find a detailed blog on AWS Security Certification and Azure Security Certification.
Here is the list of topics that we have covered in the blog.
- Cloud Security
- Common Cloud Security Threats
- Best practices for cloud security
- Benefits of Cloud Security
- AWS Security
- Azure Security
- DevSecOps
- Benefits of adopting DevSecOps
- DevSecOps Working Mechanism
Cloud Security
Cloud security is all about keeping your data, applications, and digital assets safe on cloud platforms like AWS and Azure. It includes using strong measures to ensure information stays private, accurate, and accessible. This involves things like controlling who can access data, encrypting it, securing the network, and following rules for compliance.
To do this, cloud security uses advanced tools like identity management, encryption, firewalls, and systems that watch for and respond to potential threats. Cloud providers and users share the responsibility for security, with clear rules for who’s responsible for what.
As more businesses migrate to the cloud, ensuring top-notch cloud security is critical to protecting against new cyber threats and maintaining trust in digital operations.

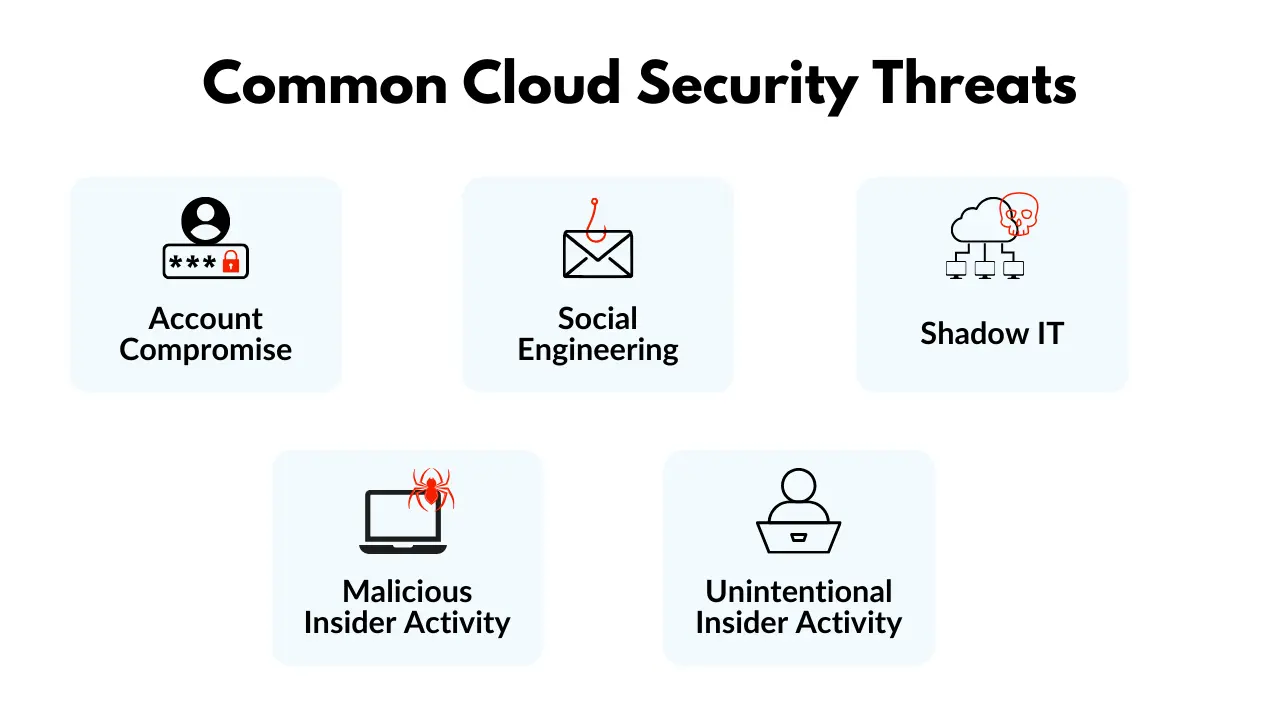
Common cloud security threats
The most common cloud security threats are:
1. Account Compromise: Attackers get access to data and systems by hijacking accounts, exploiting weak passwords, or employing brute-force methods.
2. Social Engineering: Phishing and other deceptive tactics fool employees into disclosing important information, resulting in account compromise and data breaches.
3. Shadow IT: Unauthorized cloud apps are a security issue since unpatched vulnerabilities and hacked services can result in data breaches.
4. Unintentional Insider Activity: Careless acts by employees and other parties, such as poor password habits and unauthorized app usage, can expose data and vulnerabilities inadvertently.
5. Malicious Insider Activity: Malicious insiders, whether employees or external agents, can steal data, disrupt systems, and install malware, creating a serious and difficult-to-detect hazard.
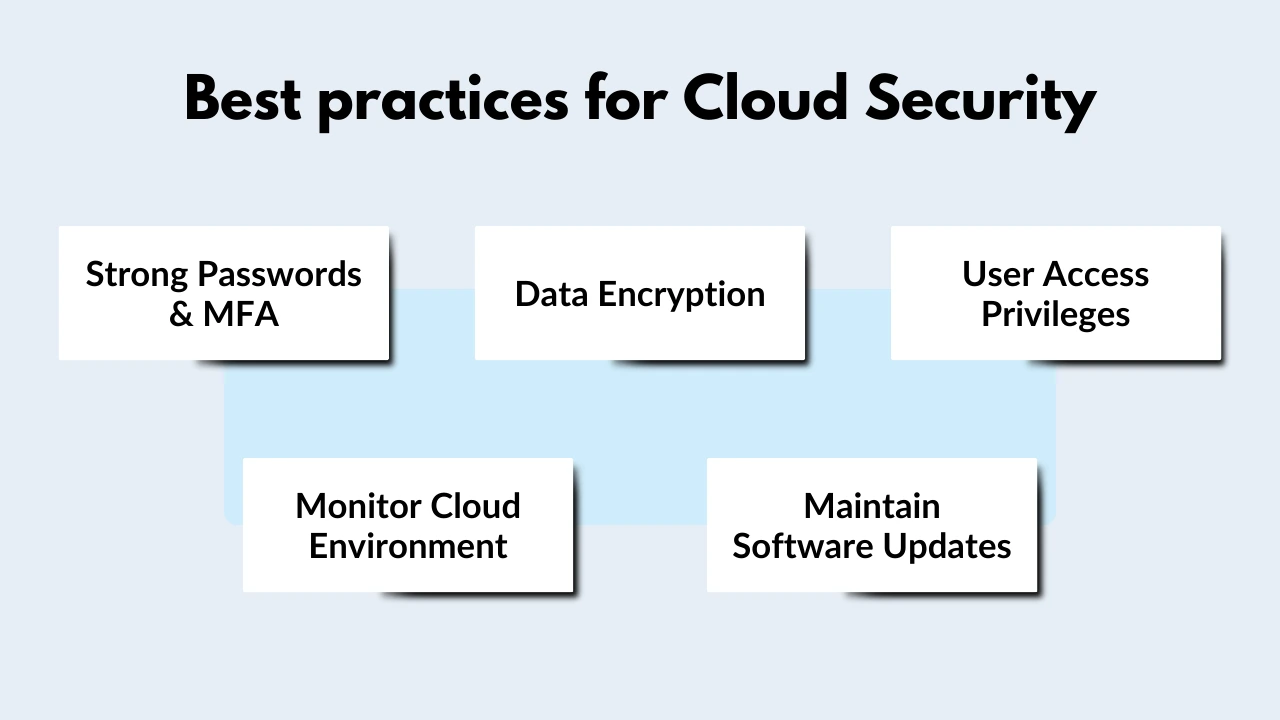
Some best practices for cloud security
Here are some cloud security recommended practices:
- Use strong passwords and multi-factor authentication (MFA): It is used to keep your cloud accounts safe from unauthorized access.
- Encrypt your data: Doing so will render it unreadable to unauthorized individuals, even if they have access to it.
- Implement least privilege access: This implies only granting users the access they require to execute their job obligations.
- Monitor your cloud environment: This will assist you in promptly identifying and responding to security issues.
- Maintain software updates: This will aid in the patching of known vulnerabilities.
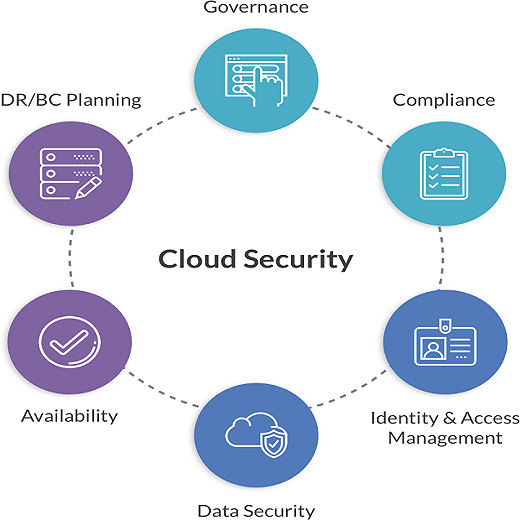
Benefits of Cloud Security
It provides numerous advantages that help to the overall resilience and security of digital operations:
- Data Security: Through encryption, access controls, and secure storage, It secures the confidentiality and integrity of data, protecting against unauthorized access and data breaches.
- IAM: Identity and access management(IAM) in cloud security ensures that the right people or systems have the appropriate level of access to cloud resources, reducing the risk of unauthorized access and data breaches.
- Cost-Efficiency: It provides a cost-effective paradigm in which organizations pay only for the services and resources they use by eliminating the need for major expenditures in physical infrastructure.
- Global Availability: It allows enterprises with scattered teams to securely access data and applications from anywhere in the globe, increasing collaboration.
- Automated Security Measures: It minimizes manual intervention by including automated security mechanisms such as threat detection and incident response, ensuring a proactive approach to possible attacks.
- Disaster Relief: Cloud-based services provides extensive disaster recovery capabilities, allowing businesses to recover data and operations quickly in the case of data loss or system failure.
- Compliance Control: Many cloud security providers follow industry-specific compliance standards, making it easier for organizations to comply with regulations without having to navigate difficult compliance concerns on their own.
AWS Security
AWS prioritizes building a secure environment for digital assets in the cloud. They provide a comprehensive range of security services, including AWS Identity & Access Management (IAM) for precise access control, AWS Key Management Service (KMS) for encryption, AWS Web Application Firewall (WAF) for web application protection, Amazon GuardDuty for continuous threat monitoring, and AWS Config for security compliance.
It works on a shared responsibility paradigm, which means that both AWS and users have defined roles in maintaining security, with AWS in charge of securing the cloud infrastructure and users in charge of safeguarding their data and applications.

Azure Security
Azure prioritizes security as well, with an emphasis on protecting digital assets across the cloud. User identities and access are managed by Azure Active Directory, while keys are securely stored by Azure Key Vault. To detect and respond to possible threats, the Azure Security Centre provides continuous monitoring and response capabilities.
DevSecOps
DevSecOps, short for Development, Security, and Operations, is an approach to software development that integrates security practices throughout the entire development lifecycle. Unlike traditional models where security is often treated as a separate phase, DevSecOps emphasizes collaboration and communication between development, security, and operations teams.
This methodology ensures that security measures are implemented from the early stages of development, enabling faster and more secure delivery of software. It involves automation, continuous monitoring, and a shared responsibility model to identify and address security issues proactively, fostering a culture where security is an integral part of the development and deployment process.
The benefits of adopting DevSecOps
- Faster time to market: By including security from the start, organizations may find and address vulnerabilities early in the development process, shortening the time necessary for security testing and assuring faster deployment.
- Improves Collaboration: It encourages cross-functional collaboration among development, security, and operations teams. This collaboration improves communication, promotes a shared knowledge of security goals, and allows teams to work together towards the same goal.
- Enhanced security: It guarantees that security is not an afterthought in the development process, but rather an inherent component of it. Organizations may dramatically minimize the risk of security breaches and data breaches by continuously monitoring and resolving vulnerabilities.
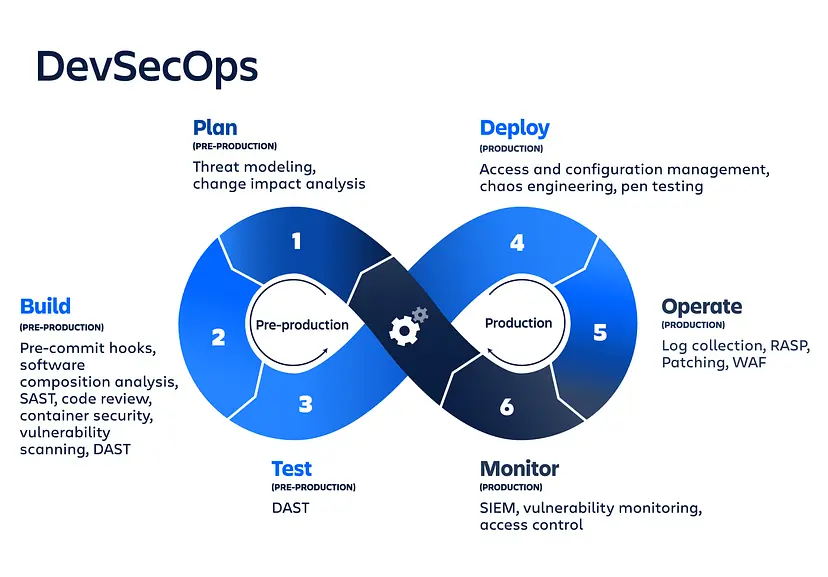
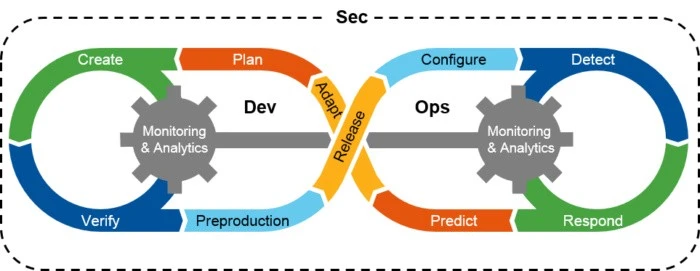
DevSecOps working Mechanism for cloud security
- Integrating Security Early: It incorporates security practices from the beginning of the software development process in order to detect and eliminate vulnerabilities as early as possible.
- Automating Security Testing: It employs automated tools and methods for continuous security testing and monitoring throughout the development lifecycle.
- Fostering Collaboration: It encourages collaboration among development, security, and operations teams, ensuring that security is a shared responsibility.
Related Links/References:
- AWS Certified Security – Specialty (SCS-C02) Exam
- AZ500: Microsoft Azure Security Technologies
- AWS Certified Solutions Architect Associate SAA-C03
- AWS Free Tier Account
- Azure Free Account
- DevSecOps Overview & Important Tools
Next Task For You
Begin your journey toward Cloud Security (AWS/Azure) including the DevSecOps Job Oriented Training Program, Connect with our Expert by clicking on the image below.






![Microsoft Agentic AI Business Solutions Architect [AB-100] | K21 Academy](https://test.k21academy.com/wp-content/uploads/2025/11/Microsoft-Agentic-AI-Business-Solutions-Architect-AB-100-Exam-Overview1.png)



