![]()
In this blog post, we will delve into the concept of Shielded Instances, explore their significance, and discuss how they contribute to a fortified cloud infrastructure.
In today’s world, keeping data safe is super important for businesses. They’re always looking for strong ways to protect their important information. Oracle Cloud, a big player in the computer cloud world, takes on this challenge with its cool Shielded Instances. These instances are like extra bodyguards for your important work, making sure it stays private and safe.
In this blog post we will cover :
- Overview of the Compute Service
- Key Features & Components
- Instance Types
- Working of Shielded Instances
- Features of Shielded Instance
- Advantages of Oracle Cloud Shielded Instances
- Conclusion
Overview of the Compute Service
Oracle Cloud Infrastructure Compute permits you to provision and manages to compute hosts, named as instances. you’ll be able to create instances as needed to satisfy your compute and application necessities. once you create an associate instance, you’ll access it firmly from your laptop, restart it, attach and detach volumes, and terminate it once you’re through with it. Any changes created to the instance’s local drives are lost once you terminate it. Any saved changes to volumes connected to the instance are preserved.
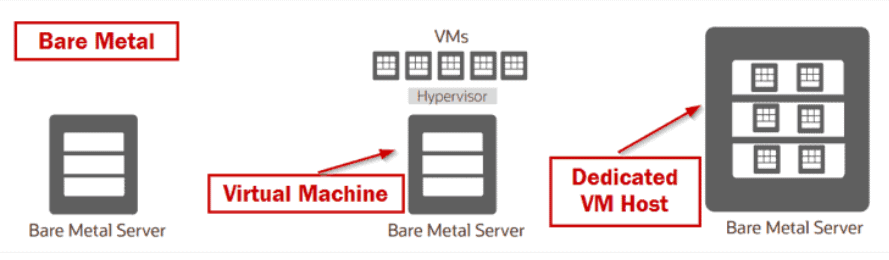
Oracle Cloud Infrastructure offers each bare metal and virtual machine instance:
- Bare Metal: A bare metal computes instance provides you dedicated physical server access for the most effective performance and powerful isolation.
- Virtual Machine: A virtual machine (VM) is associate with freelance computing surroundings that run on top of physical bare-metal hardware. The virtualization makes it potential to run multiple VMs that are isolated from one another.
An Oracle Cloud Infrastructure VM compute instance runs on equivalent hardware as a bare metal instance, leverage similar cloud-optimized hardware, firmware, software stack, and networking infrastructure.
Key Features & Components:
- UEFI Secure Boot: Shielded Instances utilize Unified Extensible Firmware Interface (UEFI) Secure Boot, a security standard that ensures the integrity of the boot process. This feature prevents the loading of unauthorized boot loaders or operating systems, safeguarding the VM from potential compromise during startup.
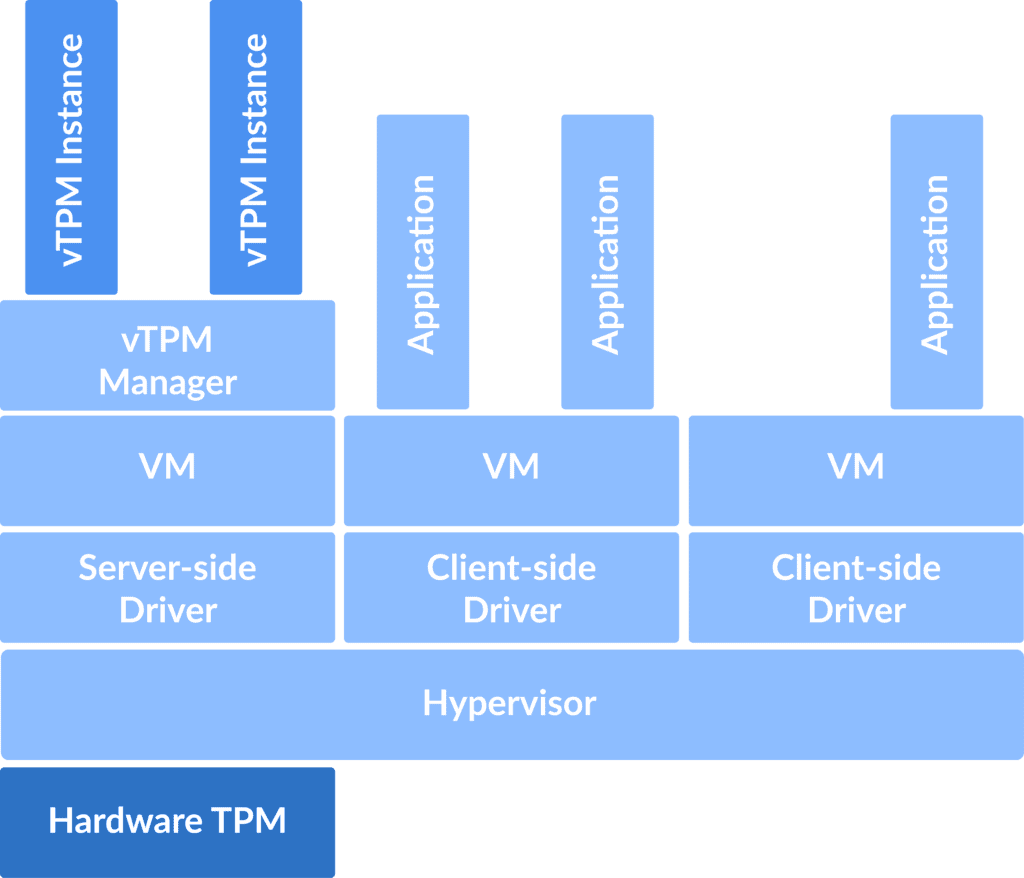
- Trusted Platform Module (TPM): Oracle Cloud Shielded Instances incorporate TPM, a hardware-based security feature that provides a secure environment for key generation, storage, and cryptographic operations. TPM enhances the overall security posture by protecting sensitive information, such as encryption keys, from unauthorized access.
- Virtual Trusted Platform Module (vTPM): The virtual TPM feature extends the benefits of TPM to virtualized environments. Shielded Instances leverage vTPM to enhance the security of VMs, ensuring that cryptographic operations within the virtualized space remain protected.
- Attestation Service: Oracle Cloud Shielded Instances include an attestation service that verifies the integrity of the hypervisor and other components during the VM boot process. This service helps in establishing trust and ensuring that the VM is running in a secure environment.
Instance Types
1. Secure Boot
Secure Boot is a Unified Extensible Firmware Interface (UEFI) feature that forestalls unauthorized boot loaders and operating systems from booting. Secure Boot validates that the signed firmware’s signature is correct before booting to stop rootkits, boot kits, and unauthorized software packages from running before the OS loads.
Rootkits are low-level malware that runs in kernel mode. Bootkits change the system bootloader and the system boots with the bootkit instead of the bootloader. Rootkits and bootkits have equivalent privileges as the OS and can record functions like keystrokes and native sign-ins.
2. Measured Boot
Measured Boot is complementary to Secure Boot. To provide the strongest security, enable both Measured Boot and Secure Boot. Secure Boot ensures that each component in the boot process features a signature that’s in the list of valid signatures. Measured Boot allows you to track boot measurements so as to know what firmware you’ve got and when it changes.
Measured Boot enhances boot security by storing measurements of boot components, like bootloaders, drivers, and operating systems. The first time you boot a shielded instance, Measured Boot uses the initial measurements to make a baseline. The baseline measurements also are referred to as golden measurements.
It uses a Trusted Platform Module (TPM) to store its measurements firmly.
3. Trusted Platform Module
Trusted Platform Module (TPM), a specialized security chip utilized by Measured Boot to store the boot measurements. On VM instances, once you change Measured Boot, the trusted Platform Module is instinctively enabled, as TPM is essential by Measured Boot.
Measurements taken by Measured Boot are kept in Platform Configuration Registers (PCRs) within the TPM. A PCR is also a memory location inside the TPM used to hold a value that summarizes all the results that were given to it in the order they were presented.






![Microsoft Agentic AI Business Solutions Architect [AB-100] | K21 Academy](https://test.k21academy.com/wp-content/uploads/2025/11/Microsoft-Agentic-AI-Business-Solutions-Architect-AB-100-Exam-Overview1.png)